Note: ATP also applies to content beyond just Exchange Online–with capabilities of protecting content across Office 365 apps such as SharePoint and OneDrive also. The first feature we will explore is the new Anti-Phishing measures, which you can configure from the 365 Admin portal Admin centers Security & Compliance. Estimated time to. We have an Office 365 E3 subscription. When clicking on a link in e-mails (Outlook desktop or OWA) one of my users get's the following error: This is a well know link to an industry association.
Cybersecurity Ventures, a computer and network security organization in California has predicted that by the end of 2022, the number of internet users would be around 6 billion. It roughly translates to about 75 percent of the total world population. Everyone is moving towards the digital era and welcoming the latest technology with both hands. But still, some organizations are yet to upgrade their security posture to defend against the latest security threats.
On the other hand, cybercriminals are also welcoming the growing trend of digitalization. More users mean more targets for them, and they take advantage of the development in mainstream IT to hone their craft. As a result, cybercrimes like phishing have evolved into a significant issue for everyone, including small, midsized, and even huge corporate firms, too. Although organizations are deploying sophisticated measures to protect themselves from these threats, success depends on the human resource – the employees who are the end-users in every enterprise. It is estimated that 90 percent of the security breaches that happen in enterprises across the globe is because of a human error. Employees expose their credentials or other sensitive information by clicking on malicious links or downloading harmful attachments.
This is where Microsoft’s Advanced Threat Protection for Office 365 can play a massive role in protecting its users and their online applications – emails and data – using intelligent solutions.
Office 365 Phishing Protection
Microsoft Office 365 Advanced Threat Protection is an advanced email filtering service hosted on the cloud. It provides a complete cover for organizations from malware, virus, and other phishing attacks.
Its unique zero-day protection feature provides enterprises with real-time analysis and protection from malicious links. It also comes equipped with a unique URL tracing feature that allows administrators to monitor all kinds of linked URLs to prevent attacks and penetrations happening inside the organization.
Some of the features provided by Microsoft’s Advanced Threat Protection are as given below:
Safe Links

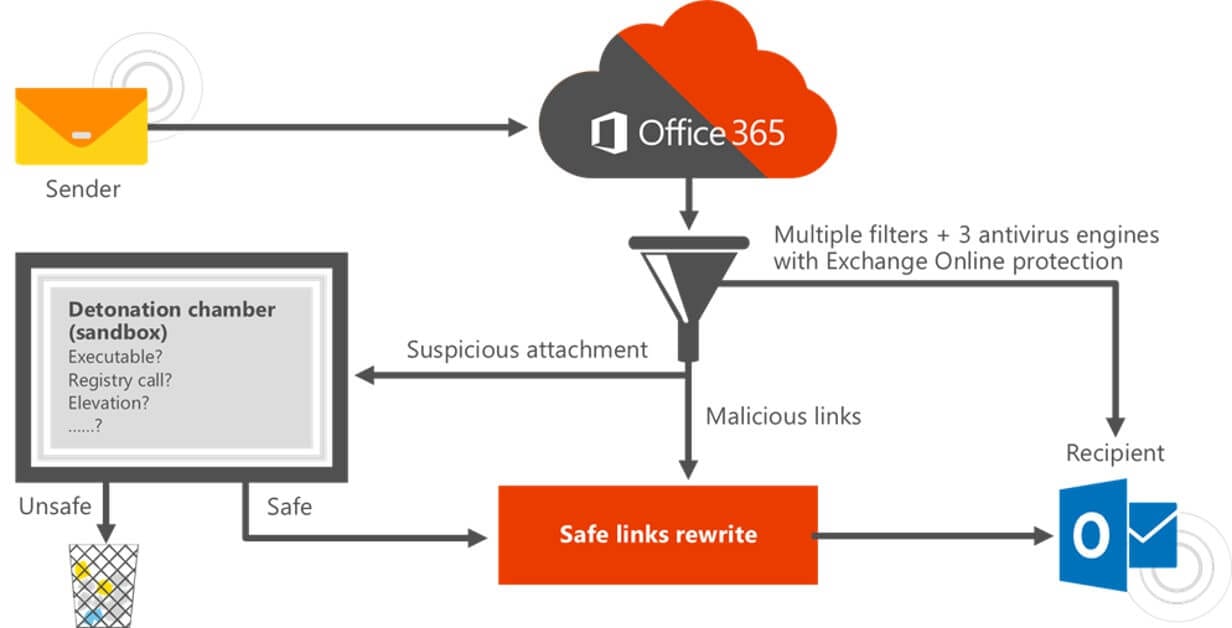
One of the significant highlights of Office 365 phishing protection is the safe links feature. It offers the ultimate security against all kinds of malicious links in your emails and other office documents.
The ATP is built similarly to the firewalls used for web-protection. It provides a protection feature called time-of-click verification of URLs. What this means is that when the recipient clicks on a link, the ATP scans and analyzes the URL to which the link leads before allowing the web page to open. It allows safe URLs to open but dynamically blocks phishing websites and suspicious URLs.
Safe Attachments
Newly launched malware and viruses can easily bypass anti-virus software and other scanning engines because the filters and scanners do not have anything in their databases to detect these. The anti-virus software or filter need to classify them and upload their virus signatures into their filter databases first. Only then can they identify and block these viruses and the attachments containing them.
But with the Microsoft Office Advanced Threat Protection, a malicious email does not enter the user’s inbox just because the existing database does not see it as suspicious. The office 365 ATP anti-phishing checks every email for unsafe attachment. It blocks the known threats and quarantines all other emails in a sandboxed virtual environment. There, it uses AI and machine learning to analyze their contents and continuously monitors the emails and their attachments. It releases each email to the user’s inbox only if it detects no suspicious activity and considers the email to be safe.
Spoof Intelligence
Spoof intelligence is another highlight of the Advanced Threat Protection software that helps in detecting spoof emails. The feature continuously monitors all incoming emails and those that are circulating within the organization. With the spoof intelligence feature, the ATP enables the users to quickly detect spoofing of domains that belong to them as well as that of external domains.
The consequences of having your domain spoofed can be severe because the sender can send just about anything in your name. However, businesses may also have genuine requirements of spoofing, such as when an enterprise hires an external firm to manage its marketing campaigns. The ATP caters to both malicious and legitimate spoofing by allowing the user to either block the sender or take no action. Whatever the case may be, the ATP’s spoof intelligence will detect any spoofing and leave it at the user’s hands to deal with it.
Anti-Phishing Policies
Microsoft ATP has default policies that apply to all the Office 365 users. However, the users can customize these based on their requirements and organization environment. The customized policies then take precedence over the default ones. The users can also edit, delete, or add to the policies whenever the need arises. Enterprises can customize or make changes to their policies easily from the Office 365 Security & Compliance Center.
Real-Time Reports
Microsoft Advanced Threat Protection provides an advanced reporting dashboard that allows administrators to view the performance of the ATP in the form of reports. Some of the report formats available in the ATP include:
Microsoft Office 365 Login
- Threat Explorer
- Threat Protection Status Report
- ATP File Types Report
- ATP Message Disposition Report
Exchange Online Advanced Threat Protection
Organizations can deploy the Office 365 phishing protection and the Advanced Threat Protection to support their applications across multiple platforms. Users of any SMTP mail transfer agent, like the Microsoft Exchange Server, can use the ATP’s protection. This cross-platform usability means that you can use the ATP as Exchange online advanced threat protection.
Conclusion
The Microsoft Office 365 phishing protection uses Artificial Intelligence and machine learning models to study the environment and adapt itself based on how the organization utilizes data. It is not a universal solution to protect against all kind of malicious attacks. But it is undoubtedly a great tool to provide security against unknown viruses and malware.
For flexible per-user pricing, PhishProtection’s integrated email security solution protects your employees from business email compromise (BEC) and many other email threats. 24×7. On any device. With features you’d expect in more expensive solutions:
All Plans Come With
- Stops business email compromise (BEC)
- Stops brand forgery emails
- Stop threatening emails before they reach the inbox
- Continuous link checking
- Real-time website scanning
- Real time alerts to users and administrators
- Protection with settings you control
- Protection against zero day vulnerabilities
- Complete situational awareness from web-based console
Phish Protection works with System Administrators, IT Professionals and IT Executives in thousands of companies worldwide. Sign up and protect your organization from phishing attacks in less than 5 minutes
-->Important
The improved Microsoft 365 security center is now available. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 security center. Learn what's new.
Applies to
Note
This topic is intended for admins. For end-user topics, see Overview of the Junk Email Filter and Learn about junk email and phishing.
In Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations without Exchange Online mailboxes, email messages are automatically protected against spam (junk email) by EOP.
Microsoft's email safety roadmap involves an unmatched cross-product approach. EOP anti-spam and anti-phishing technology is applied across our email platforms to provide users with the latest anti-spam and anti-phishing tools and innovations throughout the network. The goal for EOP is to offer a comprehensive and usable email service that helps detect and protect users from junk email, fraudulent email threats (phishing), and malware.
As email use has grown, so has email abuse. Unmonitored junk email can clog inboxes and networks, impact user satisfaction, and hamper the effectiveness of legitimate email communications. That's why Microsoft continues to invest in anti-spam technologies. Simply put, it starts by containing and filtering junk email.
Tip
The following anti-spam technologies are useful when you want to allow or block messages based on the message envelope (for example, the sender's domain or the source IP address of the message). To allow or block messages based on payload (for example, URLs in the message or attached files), then you should use the Tenant Allow/Block List portal.
Anti-spam technologies in EOP
To help reduce junk email, EOP includes junk email protection that uses proprietary spam filtering technologies to identify and separate junk email from legitimate email. EOP spam filtering learns from known spam and phishing threats and user feedback from our consumer platform, Outlook.com. Ongoing feedback from EOP users in the junk email classification program helps ensure that the EOP technologies are continually trained and improved.
The anti-spam settings in EOP are made of the following technologies:
Connection filtering: Identifies good and bad email source servers early in the inbound email connection via the IP Allow List, IP Block List, and the safe list (a dynamic but non-editable list of trusted senders maintained by Microsoft). You configure these settings in the connection filter policy. Learn more at Configure connection filtering.
Note
Spoof intelligence uses connection filtering to create allow and block lists of senders who are spoofing your email domain. For more information, see Learn more about spoof intelligence in Microsoft 365.
Spam filtering (content filtering): EOP uses the spam filtering verdicts Spam, High confidence spam, Bulk email, Phishing email and High confidence phishing email to classify messages. You can configure the actions to take based on these verdicts, and you can configure the end-user notification options for messages that were quarantined instead of delivered. For more information, see Configure anti-spam policies in Microsoft 365.
Note
By default, spam filtering is configured to send messages that were marked as spam to the recipient's Junk Email folder. However, in hybrid environments where EOP protects on-premises Exchange mailboxes, you need to configure two mail flow rules (also known as transport rules) in your on-premises Exchange organization to recognize the EOP spam headers that are added to messages. For details, see Configure standalone EOP to deliver spam to the Junk Email folder in hybrid environments.
Outbound spam filtering: EOP also checks to make sure that your users don't send spam, either in outbound message content or by exceeding outbound message limits. For more information, see Configure outbound spam filtering in Microsoft 365.
Spoof intelligence: For more information, see Learn more about spoof intelligence in Microsoft 365.
Manage errors in spam filtering
It's possible that good messages can be identified as spam (also known as false positives), or that spam can be delivered to the Inbox. You can use the suggestions in the following sections to find out what happened and help prevent it from happening in the future.
Here are some best practices that apply to either scenario:
Always submit misclassified messages to Microsoft. For more information, see Report messages and files to Microsoft.
Examine the anti-spam message headers: These values will tell you why a message was marked as spam, or why it skipped spam filtering. For more information, see Anti-spam message headers.
Point your MX record to Microsoft 365: In order for EOP to provide the best protection, we always recommend that you have email delivered to Microsoft 365 first. For instructions, see Create DNS records at any DNS hosting provider for Microsoft 365.
If the MX record points to some other location (for example, a third-party anti-spam solution or appliance), it's difficult for EOP to provide accurate spam filtering. In this scenario, you need to configure Enhanced Filtering for connectors (also known as skip listing). For instructions, see Enhanced Filtering for Connectors in Exchange Online.
Use email authentication: If you own an email domain, you can use DNS to help insure that messages from senders in that domain are legitimate. To help prevent spam and unwanted spoofing in EOP, use all of the following email authentication methods:
SPF: Sender Policy Framework verifies the source IP address of the message against the owner of the sending domain. For a quick introduction to SPF and to get it configured quickly, see Set up SPF to help prevent spoofing. For a more in-depth understanding of how Microsoft 365 uses SPF, or for troubleshooting or non-standard deployments such as hybrid deployments, start with How Microsoft 365 uses Sender Policy Framework (SPF) to prevent spoofing.
DKIM: DomainKeys Identified Mail adds a digital signature to the message header of messages sent from your domain. For information, see Use DKIM to validate outbound email sent from your custom domain in Microsoft 365.
DMARC: Domain-based Message Authentication, Reporting, and Conformance helps destination email systems determine what to do with messages that fail SPF or DKIM checks and provides another level of trust for your email partners. For more information, see Use DMARC to validate email in Microsoft 365.
Verify your bulk email settings: The bulk complaint level (BCL) threshold that you configure in anti-spam policies determines whether bulk email (also known as gray mail) is marked as spam. The PowerShell-only setting MarkAsSpamBulkMail that's on by default also contributes to the results. For more information, see Configure anti-spam policies in Microsoft 365.
Office 365 Atp Api
Prevent the delivery of spam to the Inbox
Verify your organization settings: Watch out for settings that allow messages to skip spam filtering (for example, if you add your own domain to the allowed domains list in anti-spam policies). For our recommended settings, see Recommended settings for EOP and Microsoft Defender for Office 365 security and Create safe sender lists.
Verify the junk email rule is enabled in the user's mailbox: It's enabled by default, but if it's disabled, messages marked as junk can't be moved into the Junk Email folder. For more information, see Configure junk email settings on Exchange Online mailboxes in Microsoft 365.
Use the available blocked sender lists: For information, see Create blocked sender lists.
Unsubscribe from bulk email If the message was something that the user signed up for (newsletters, product announcements, etc.) and contains an unsubscribe link from a reputable source, consider asking them to simply unsubscribe.
Standalone EOP: create mail flow rules in on-premises Exchange for EOP spam filtering verdicts: In standalone EOP environments where EOP protects on-premises Exchange mailboxes, you need to configure mail flow rules (also known as transport rules) in on-premises Exchange to translate the EOP spam filtering verdict so the junk email rule can move the message to the Junk Email folder. For details, see Configure standalone EOP to deliver spam to the Junk Email folder in hybrid environments.
Prevent good email from being identified as spam
Office 365 Atp Docs
Here are some steps that you can take to help prevent false positives:
Verify the user's Outlook Junk Email Filter settings:
Verify the Outlook Junk Email Filter is disabled: When the Outlook Junk Email Filter is set to the default value No automatic filtering, Outlook doesn't attempt to classify massages as spam. When it's set to Low or High, the Outlook Junk Email Filter uses its own SmartScreen filter technology to identify and move spam to the Junk Email folder, so you could get false positives. Note that Microsoft stopped producing spam definition updates for the SmartScreen filters in Exchange and Outlook in November, 2016. The existing SmartScreen spam definitions were left in place, but their effectiveness will likely degrade over time.
Verify the Outlook 'Safe Lists Only' setting is disabled: When this setting is enabled, only messages from senders in the user's Safe Senders list or Safe Recipients list are delivered to the Inbox; email from everyone else is automatically moved to the Junk Email folder.
For more information about these settings, see Configure junk email settings on Exchange Online mailboxes in Microsoft 365.
Use the available safe sender lists: For information, see Create safe sender lists.
Verify users are within the sending and receiving limits as described in Receiving and sending limits in the Exchange Online service description.
Standalone EOP: use directory synchronization: If you use standalone EOP to help protect your on-premises Exchange organization, you should sync user settings with the service by using directory synchronization. Doing this ensures that your users' Safe Senders lists are respected by EOP. For more information, see Use directory synchronization to manage mail users.
Anti-spam legislation
Office 365 Outlook Login
At Microsoft, we believe that the development of new technologies and self-regulation requires the support of effective government policy and legal frameworks. The worldwide spam proliferation has spurred numerous legislative bodies to regulate commercial email. Many countries now have spam-fighting laws in place. The United States has both federal and state laws governing spam, and this complementary approach is helping to curtail spam while enabling legitimate e-commerce to prosper. The CAN-SPAM Act expands the tools available for curbing fraudulent and deceptive email messages.
